Security Alert for Microsoft Windows Users and VPN Required for RDP
Thursday, March 22nd, 2012
There are two important consequences of a recent critical vulnerability announced by Microsoft last week:
- IS&T is implementing a policy change regarding the use of Windows’ Remote Desktop feature (RDP). If you use RDP to remotely access computers present on the BU campus, starting on Tuesday, April 3rd, 2012,  you will need to VPN into BU (http://vpn.bu.edu) before connecting. Learn more about using the VPN.
- Those managing their own Windows computer should confirm that their computer has been updated. Details for making sure you computer is up to date can be found below.
If your computer is managed by IS&T’s Desktop Services or one of our IT Partners, it is likely your work computer is up to date, and no further action is required besides following this policy after April 3rd. If you have any questions about this policy, have questions about how your computer is configured, or if you have trouble remotely connecting to a computer on campus after April 2nd, you may contact the IT Help Center by phone at 617-353-HELP (4357), email, or web for assistance.
Impact
An exploit has already been released that will cause a Blue Screen of Death on Windows 7 and a Denial of Service on Windows XP. It is expected that another exploit will soon be released that will allow an attacker to have complete control of the computer. After that, the next expected step is that a self-replicating worm will be released that will automatically jump from host to host, granting the attacker access to the system and taking any other action the attacker may wish.
Solution
If IS&T or one of our IT partners manages the computer you use, no further action is required other than following the new RDP policy starting April 3rd. If you are personally responsible for patching your computer and keeping it up to date (or if  you would like to know how to better secure your home computer), there is some additional information you should know regarding the vulnerability identified by Microsoft. Below, we have some recommended actions for you to take to ensure your computer is protected.
What IS&T and the IT Partners are Doing
- IS&T and the IT Partners have been working to install this patch on the servers at BU.
- Due to the serious nature of this vulnerability, IS&T will be blocking RDP access at the BU firewall within the next few days. This block is necessary because it is common for people to disable the automatic update functionality. It can reasonably be expected that many systems will remain unpatched for an extended period of time. If we take no action to block access to RDP through the firewall, exploit code could significantly impact the stable operation of computers at BU or otherwise compromise BU operations or protected information. (For reference, as of Monday (3/19) there were over 3000 computers at BU that had RDP up and operating.)
Action Required for all Microsoft Windows Users
- If you are running Microsoft Windows and you do not have it set to Automatically Update, you should run Windows Update immediately and confirm that you have the correct patches using the instructions below.
- If you do have Automatic Updates turned on, you should have received the patch last Tuesday and you are all set – no further action is required. If you would like, you can confirm that you are updating automatically.
- If you use Microsoft Windows Remote Desktop (RDP) to connect to a BU computer from outside of BU, you will need to connect to the VPN prior to connecting via RDP – login at http://vpn.bu.edu.
- If you have set up your system to allow remote access, or if you run a server, see the additional instructions below.
Related Instructions
If you never use RDP:
- If you do not need to use RDP, you can disable it. Â Instructions are provided below.
- If you do need to use RDP, please follow the security best practices published by IS&T:
https://www.bu.edu/tech/about/security-resources/bestpractice/remote-desktop/
Best practices include moving RDP away from its standard port to some other port protected by the BU Edge Firewall.
If you are running a server:
- Patch information can be found here: http://technet.microsoft.com/en-us/security/bulletin/ms12-020
- If the system cannot be immediately patched, please see this page for an alternative “fix it†option: http://blogs.technet.com/b/srd/archive/2012/03/13/cve-2012-0002-a-closer-look-at-ms12-020-s-critical-issue.aspx
Confirm that you have the correct patches:
Windows 7
- Go to Start -> All Programs -> Windows Update -> View Update History and confirm that KB2667402 and KB2621440 are installed

Windows XP
- Go to Start -> Microsoft Update -> Review your update history
- Confirm that KB2621440 is installed
How to disable RDP if you don’t use it:
Windows 7
- Go to Control Panel, click System And Security, and then click System.
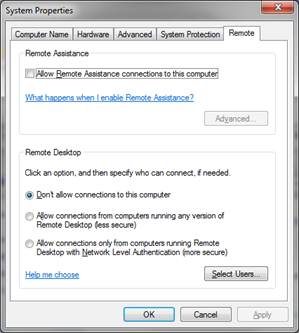
- On the System page, click Remote Settings in the left pane. This opens the System Properties dialog box to the Remote tab.
- To disable Remote Desktop, select Don’t Allow Connections To This Computer,
- Also uncheck the Allow Remote Assistance box as shown below and then click OK
Windows XP
- Click System in Control Panel.
- On the Remote tab, clear the Allow users to connect remotely to your computer check box, and then click OK.
