8 states targeted in CARES Act scams from cybercrime group
Massachusetts has been named on of the 8 states targeted in an unemployment scam. Massachusetts reported at least 17 fraudulent unemployment claims on May 15 and May 16, causing a potential loss of about $500,000. Other states are seeing a number of fake claims as well:
“Between April 15 and April 29, Scattered Canary filed at least 82 fraudulent claims for CARES Act Economic Impact Payments, which are meant to provide relief to families as a result of the COVID-19 pandemic. The only information needed by Scattered Canary to file these claims was an individual’s name, address, date of birth, and Social Security number. Of the 82 claims Scattered Canary filed, at least 30 of them were accepted by the IRS and presumably paid out”
___________________________________________________________________
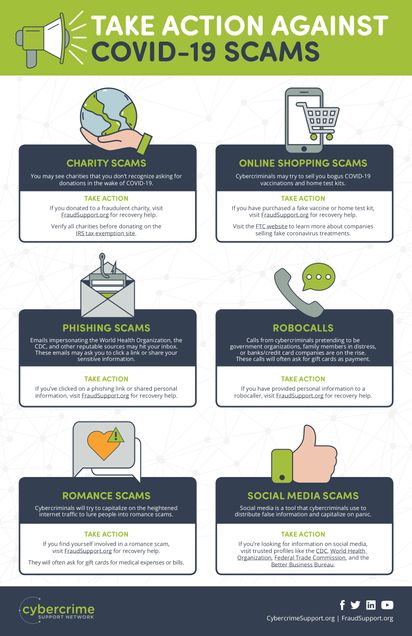
Charity scams, phishing scams, online shopping scams, social media scams and vishing scams (voice or phone call scams) have all significantly increased during this time.
Check out the infographic from cybercrimesupport.org which shows how you can take action against these scams: FraudSupport.org-COVID-19-Scams
____________________________________________________________________
Microsoft Teams Impersonation
Attackers have been impersonating notifications from Microsoft Teams in order to steal the credentials of employees. Recently, Microsoft Teams has seen one of the largest increases in users as a result of the shift to remote work given the ongoing COVID-19 pandemic.
Attackers crafted convincing emails that impersonate automated notification emails from Microsoft Teams. The landing pages that host both attacks look identical to the real webpages, and the imagery used is copied from actual notifications and emails from this provider. In one of the attacks, the sender email originates from a recently registered domain, “sharepointonline-irs.com”, which is not associated to either Microsoft or the IRS.
Why is this attack effective?
- Convincing Email and Landing Page: The email and landing page the attackers created were convincing. The webpages and the links the email direct to are visually identical to legitimate Microsoft Teams and Microsoft login pages. Recipients would be hard-pressed to understand that these sites were set up to misdirect and deceive them to steal their credentials.
- Timing: Given the current situation, people have become accustomed to notifications and invitations from collaboration software providers. Because of this, recipients might not look further to investigate the message.
- Urgency: A recipient may feel more compelled to quickly login to access the page because of the urgency felt when contacted by a coworker.
