When you log in to a Boston University Web page that requires two-factor authentication, a login screen like this will be displayed.
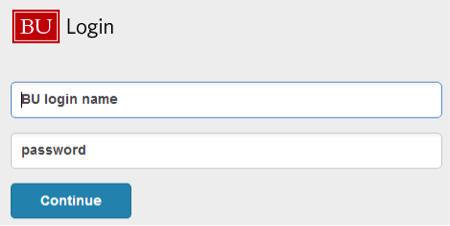
- Enter your BU login name and Kerberos password.
- Then press the Continue button.
- If you have not yet registered a device to serve as the second factor in the required two-factor authentication process, you will be directed to this enrollment screen. Read more about enrolling a device.
Log In With the Duo Universal Prompt
After completing Duo enrollment , you’ll see the Duo prompt the next time you perform a browser-based login to a web service or application protected with Duo.
The first time you log in to an application with Duo using the Universal Prompt, Duo chooses one of your configured login options automatically, selecting the most-secure method from the ones you have available.
Duo authentication methods from most to least secure:
- Touch ID
- Security keys
- Verified Duo Push
- Duo Mobile push approval
- YubiKey passcodes
- Duo Mobile generated passcodes
- Hardware token passcodes
- SMS passcodes
- Phone call approval
Duo considers Touch ID and security keys to be the most secure authentication methods, so if you have set up either of these methods and the application allows their use you’ll automatically see the prompt to use your fingerprint with Touch ID or tap your security key the first time you log into that application.
The next most secure Duo method is using Duo Mobile to approve push notifications. If you do not have Touch ID or a security key available, but you do have a phone or tablet with Duo Mobile activated, the Universal Prompt will automatically send you a Duo Push the first time you log in to that application. You may have to enter a code to approve the push request if your organization requires it.
If you haven’t set up Duo Mobile, then the Duo Universal Prompt automatically selects your next available option, following the most to least secure preference order.
If you don’t want to use the method Duo automatically suggests for that application, cancel the Duo authentication in progress and click or tap Other options. Then, select the method you want from the list.
Completing Duo login sets the login option you used as the first choice for this application. Future Universal Prompt logins to that application from the same device and browser will automatically use that same method. If you cancel the authentication in process and choose a different device, then the device you use becomes the first choice for that application.
There is no way to turn off automatic device selection, or to explicitly configure a default authentication device.
Your organization’s Duo administrator may choose to block some authentication options for certain applications, requiring that you choose a different device. Since Duo remembers the last-used authentication device for each application you access, the Universal Prompt should always display the right default option for that application.
Choose a Different Method
If you ever want to choose a different device or Duo method than the one shown automatically by the Universal Prompt, click Other options near the bottom. This takes you to a list of all your available Duo authentication options. Click on the one you want to use and follow the instructions shown to complete logging in to the application.
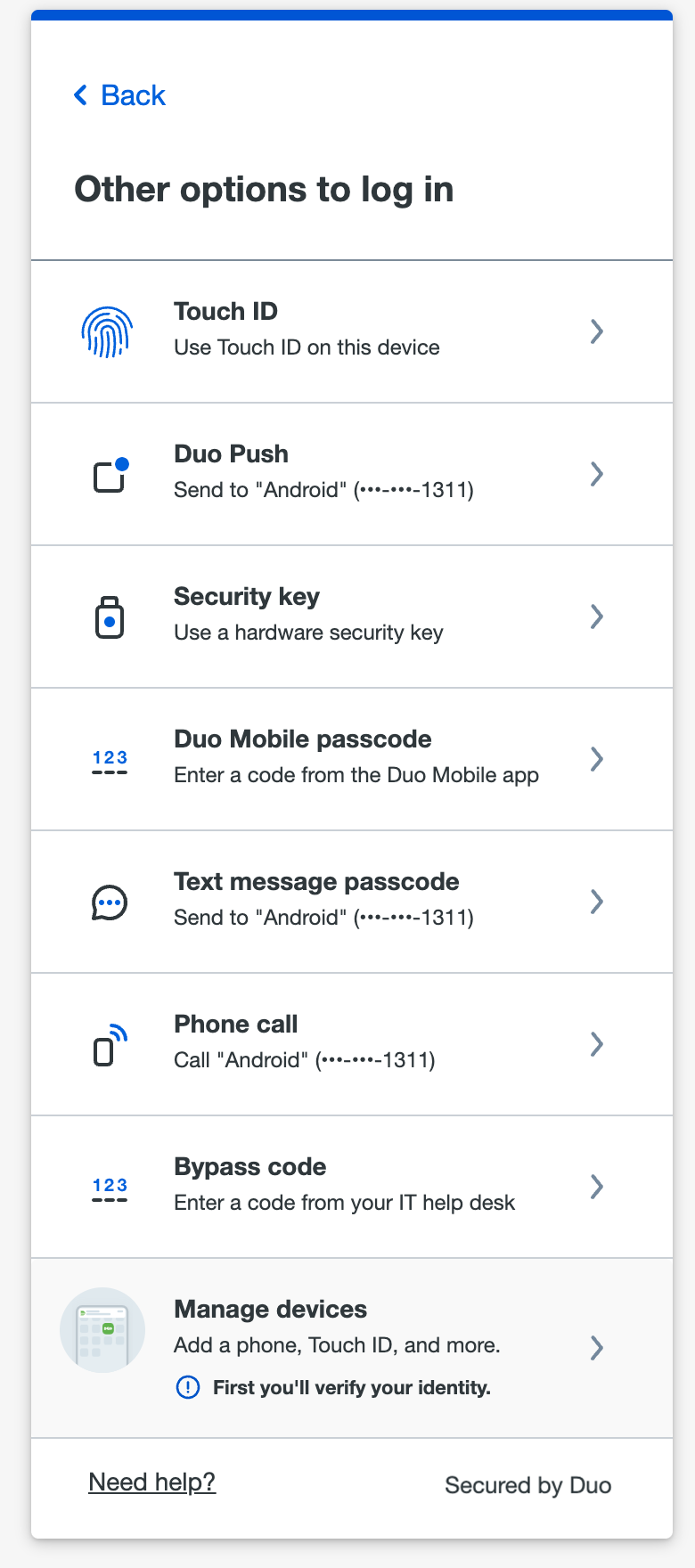
Your organization might apply a policy that prevents the use of some authentication methods for one or all applications. If so, those options won’t show up in the list.
Remembered Devices
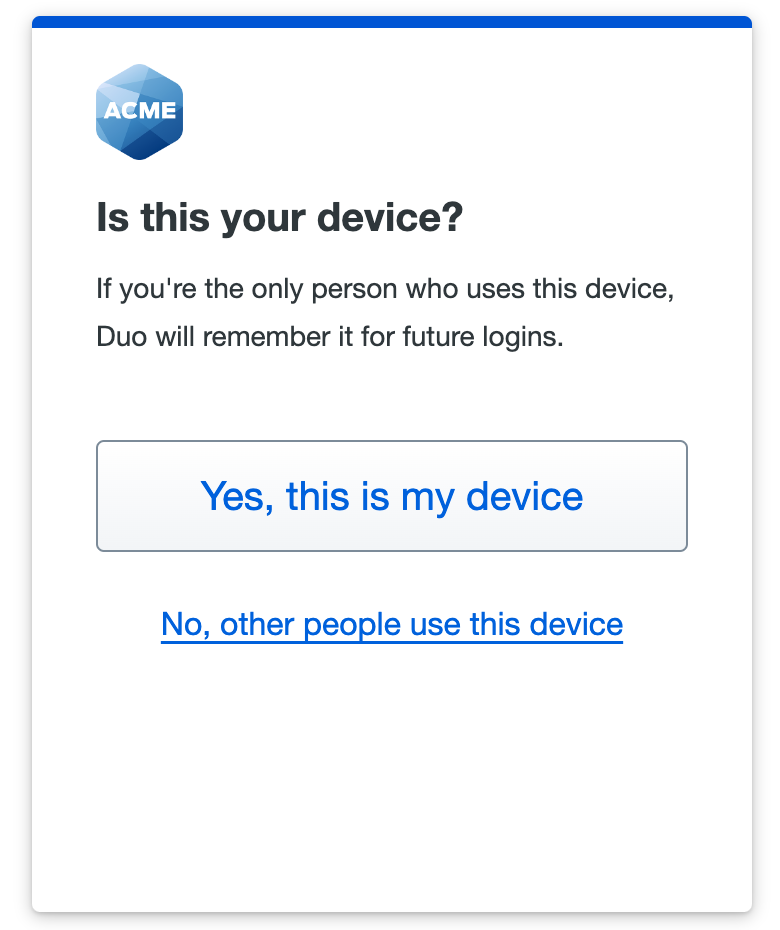
If your organization’s policy allows it, you may be able to skip authenticating with Duo again for a set amount of time. The first time you approve the Duo authentication request, you’ll see the option to remember your device.
Choose Yes, this is my device to create a trusted device session that will let you skip Duo two-factor authentication when you log in again with the same browser and device until that remembered device session expires.
Depending on the policy applied by your Duo administrator, this may remember your device across all your organization’s Duo-protected applications, or there may be unique policies applied to applications that require you to perform Duo authentication again regardless of whether you remembered the device. Ask your Duo administrator or help desk for more information.
Do not trust the device when using a public or shared computer! This could leave your Duo session available to other users. Remember the device only when you access applications from your own computer.
Clicking on No, other people use this device will not create a trust session. You won’t be asked to remember that device again for 14 days.
When your trusted browser session expires, you will need to use two-factor authentication again. Duo Push, phone call, text message, and passcode authentication methods will show the option to remember the device already enabled for you. Leaving the option enabled creates a new remembered device session.
If you don’t want to remember the device anymore, uncheck the Remember me box before you approve the Duo Push or phone call request or enter a passcode.
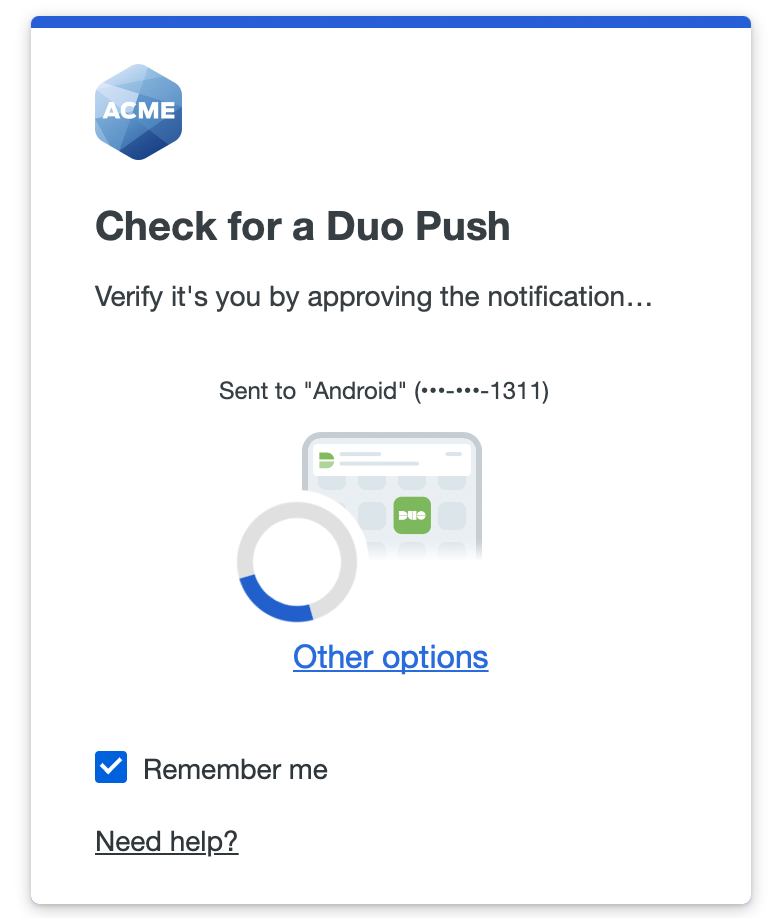
If you log in automatically with a WebAuthn method like Touch ID, a passkey, or a security key you won’t see the Remember me option on the page. You will need to cancel the Duo authentication in progress if you don’t want to remember that device anymore. This sends you back to the page where you can uncheck the Remember me box and then try to log in again.
Duo Universal Prompt Login Options
Availability of the following Duo login options in the Universal Prompt depends on your browser or browser version, or on the policies applied by your organization’s Duo administrator.
Duo Push
Pushes a login request to your iOS or Android phone or tablet if you have Duo Mobile installed and activated. Review the request on your phone or tablet and tap Approve to log in to the application.
Verified Duo Push
Your organization may wish for you to enter a verification code shown within the Duo Universal Prompt into Duo Mobile when you approve a Duo Push request. This protects you from approving login requests not made by you and helps keep your accounts and information safe.
If your organization requires Duo Push verification, Duo Universal Prompt displays a numeric code three to six digits in length on-screen when you choose to use Duo Push to log in to that application.
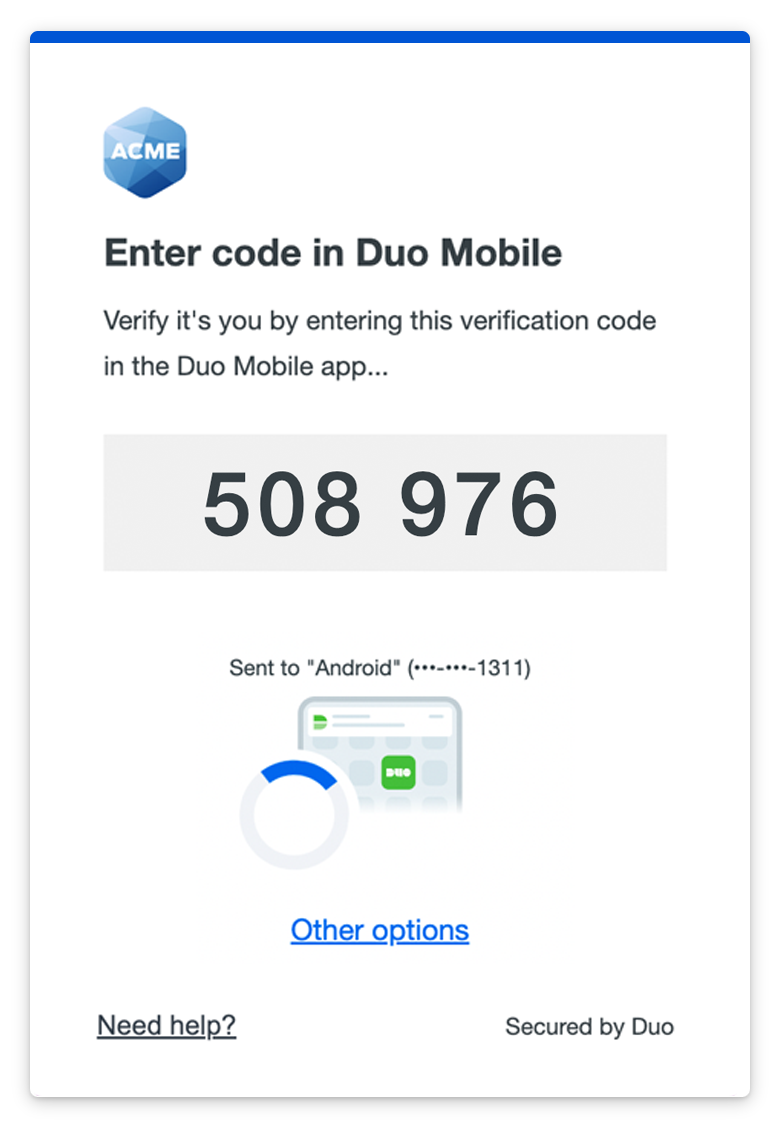
Enter the code shown on your screen into the Duo Push request received on your Android or iOS device. Android users only: tap Verify to finish approving the login request.
Security Key
A security key plugs into your USB port and when tapped or pressed it sends a signed response back to Duo to verify your login. Duo uses the WebAuthn authentication standard to interact with your security keys. You may also see WebAuthn referred to as “FIDO2”.
In order to use a security key with Duo, make sure you have the following:
- A supported browser (check the table above to verify your browser supports security keys).
- An available USB port.
- A WebAuthn/FIDO2 security key. WebAuthn/FIDO2 security keys from Yubico or Feitian are good options. U2F-only security keys (like the YubiKey NEO-n) are not supported.
Insert your security key if not already plugged in, and then tap or press your security key when prompted to log in to the application. Some types of keys flash as a prompt for you to authenticate. Your browser may also pop up a prompt instructing you to tap your security key.
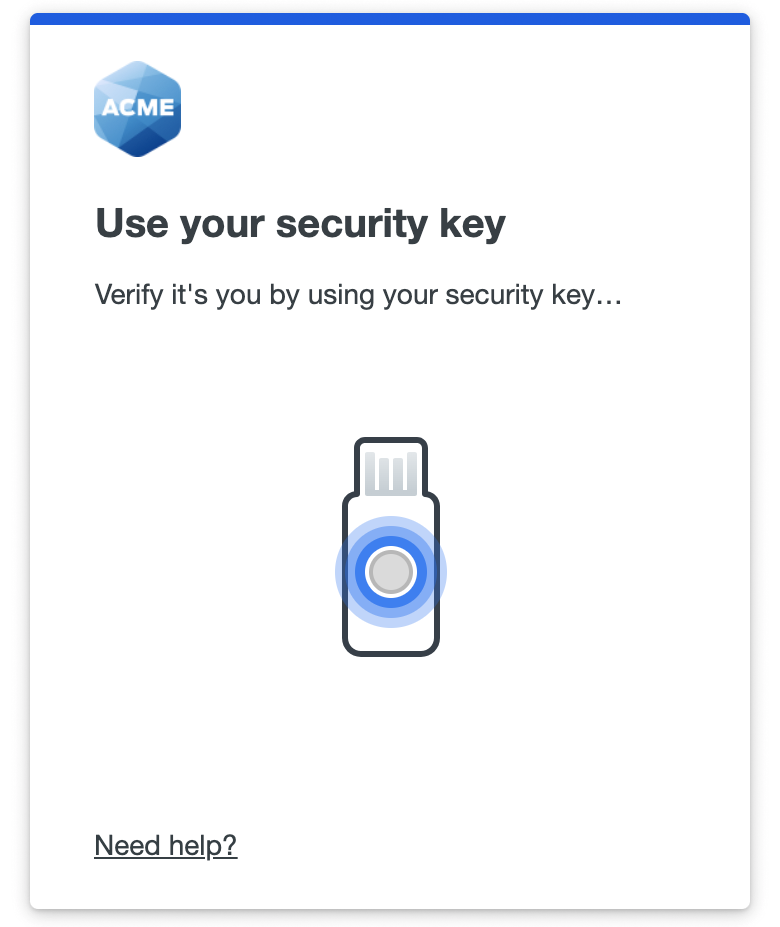
You need to interact with the prompt to use a security key from Safari browser on macOS or any browser on iOS. Click or tap the Use security key button and then tap or press your security key.
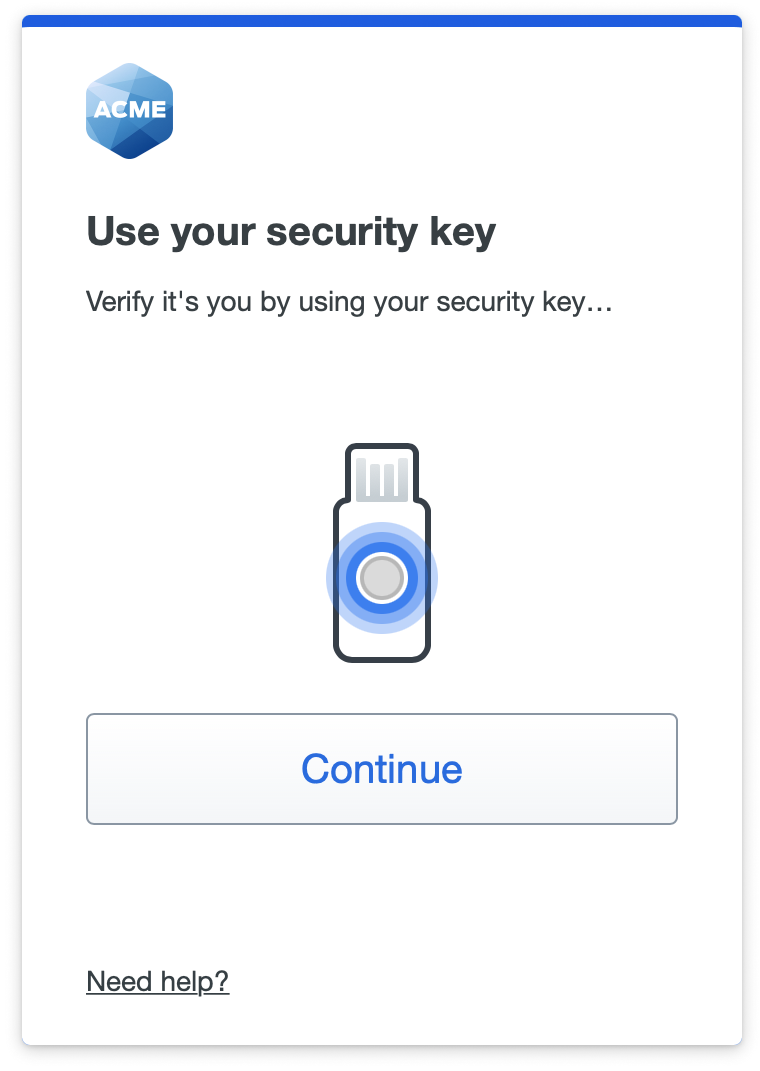
If you need to cancel a security key authentication in progress, click or tap the cancel option shown by your browser, outside of the Duo Universal Prompt.
Fingerprint Sensor
Fingerprint authentication lets you use your device’s fingerprint sensor for Duo login verification. Duo supports fingerprint verification with Touch ID on Apple MacBooks and Magic Keyboards.
Touch ID
In order to use Touch ID with Duo, make sure you have the following:
- A MacBook Pro, MacBook Air, or Magic Keyboard with a Touch ID button.
- A fingerprint enrolled in Touch ID (see how to do this at the Apple Support site).
- Chrome 70 or later. While Duo Passwordless supports Touch ID in Safari, use of Touch ID for two-factor authentication in Safari and additional browsers on macOS is not available today.
Touch your Mac’s Touch ID sensor when prompted to log in to the application. If you aren’t able to access the Touch ID sensor (such as when you close and dock your laptop), then you can choose to type in your Mac login password instead to verify.
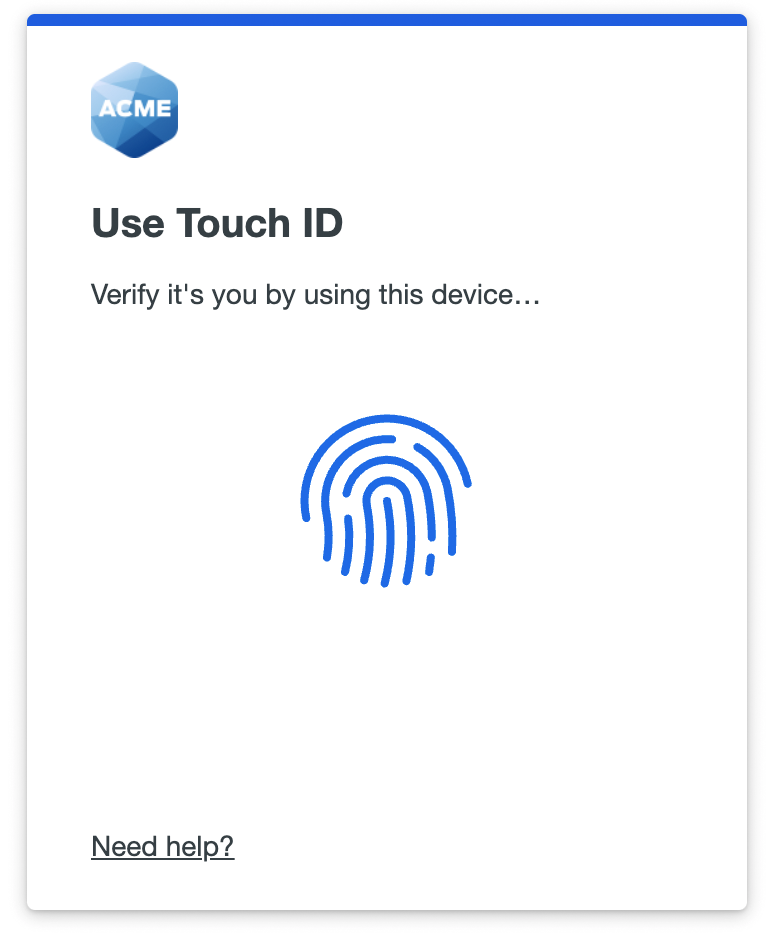
If you need to cancel a Touch ID authentication in progress, click or tap the cancel option shown by your browser, outside of the Duo Universal Prompt.
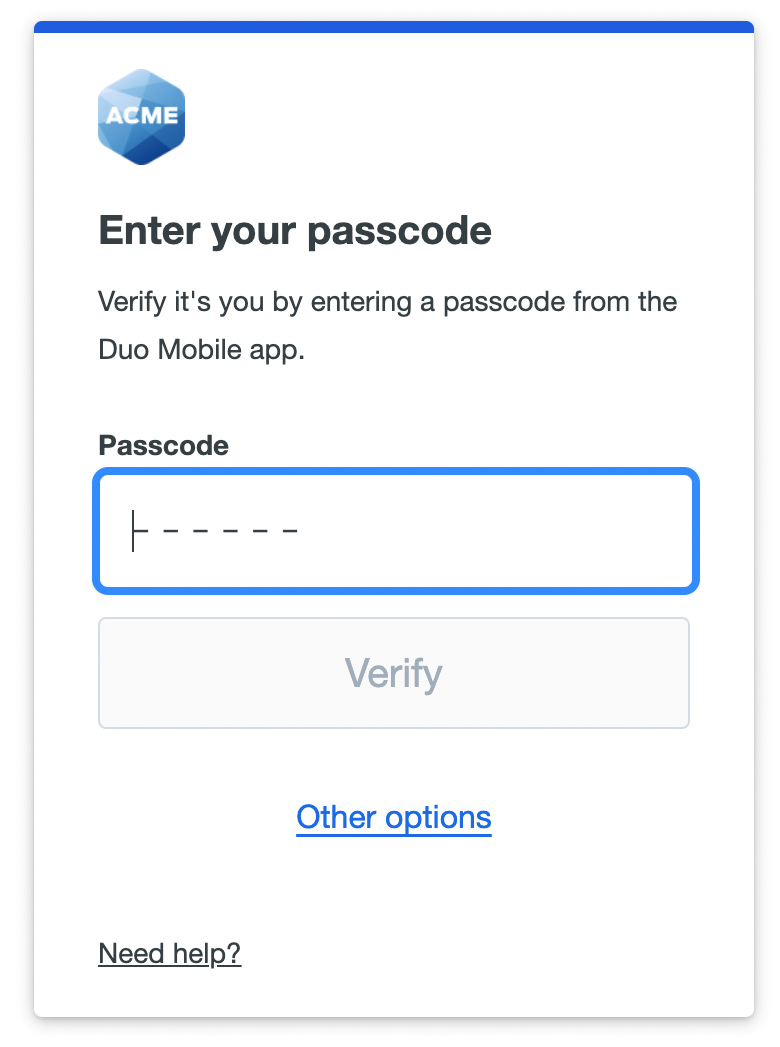
Duo Mobile Passcode
Log in using a passcode generated by the Duo Mobile app installed and activated on your Android or iOS device. Open Duo Mobile and locate your organization’s account in the accounts list, and tap it to generate a six-digit passcode. Enter that passcode into the space provided and click or tap Verify to log in to the application.
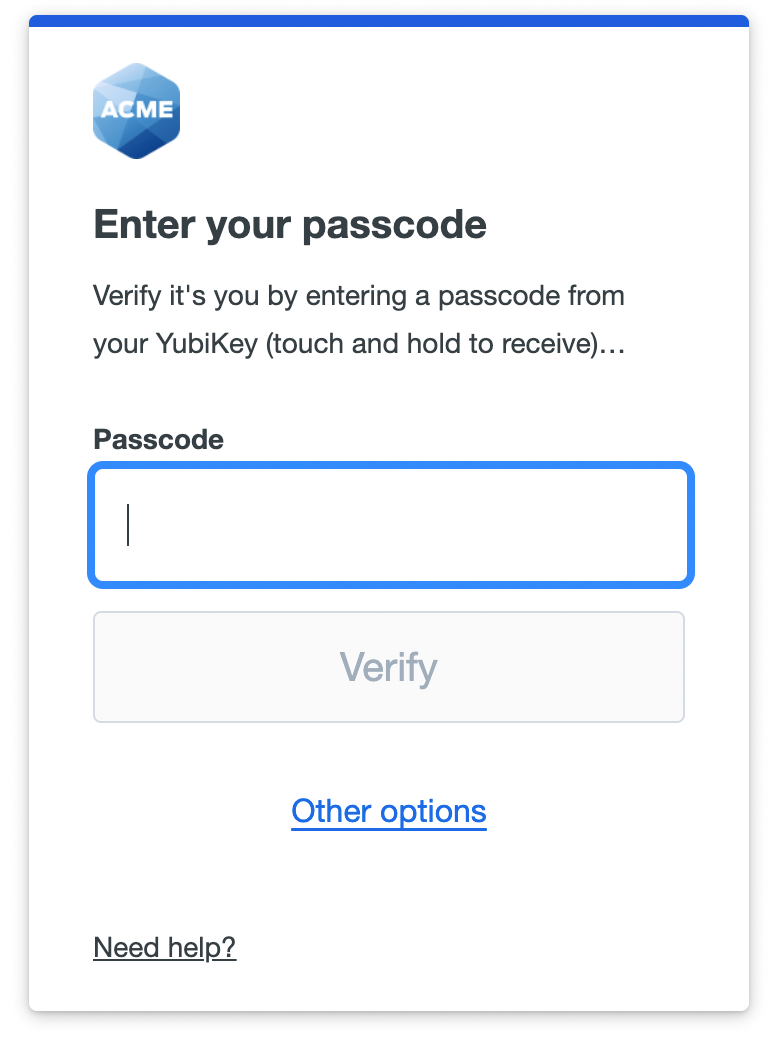
YubiKey Passcode
Log in using a passcode generated by a YubiKey. Connect or plug in your YubiKey and press it to generate and submit a passcode to log in to the application.
Your administrator must have configured the YubiKey for passcode use in Duo. This is a separate function from using a YubiKey as a security key.
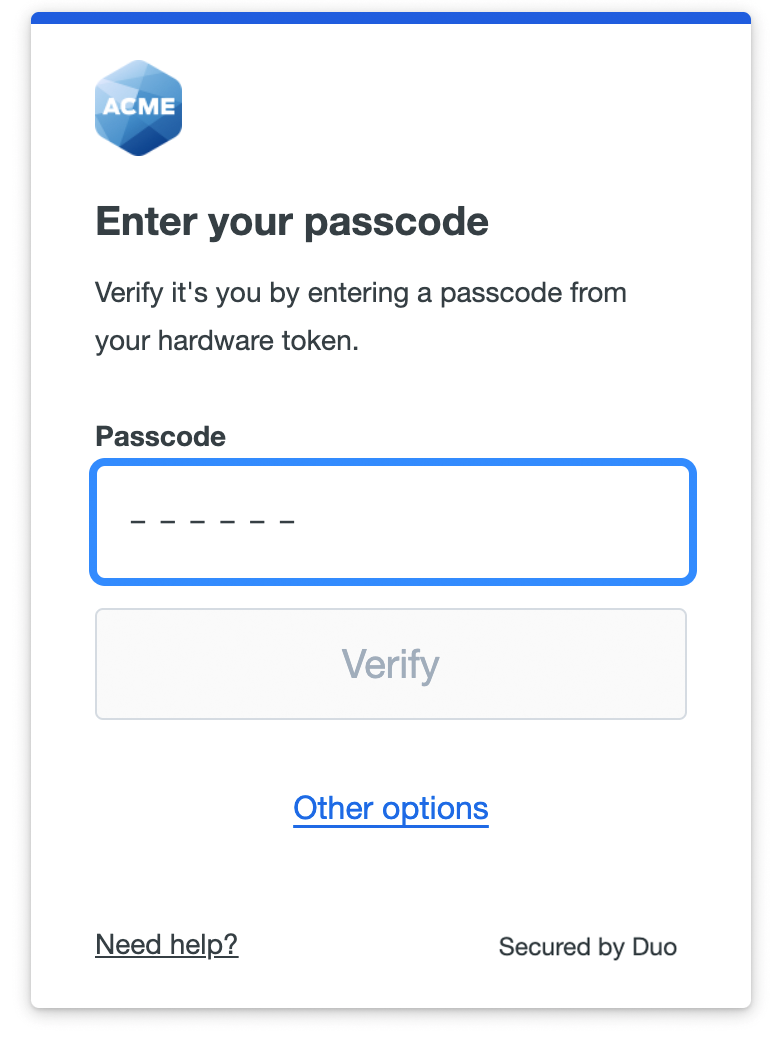
Hardware Token Passcode
Log in using a passcode generated by a hardware token provided to you by your organization. Enter that passcode into the space provided and click or tap Verify to log in to the application.
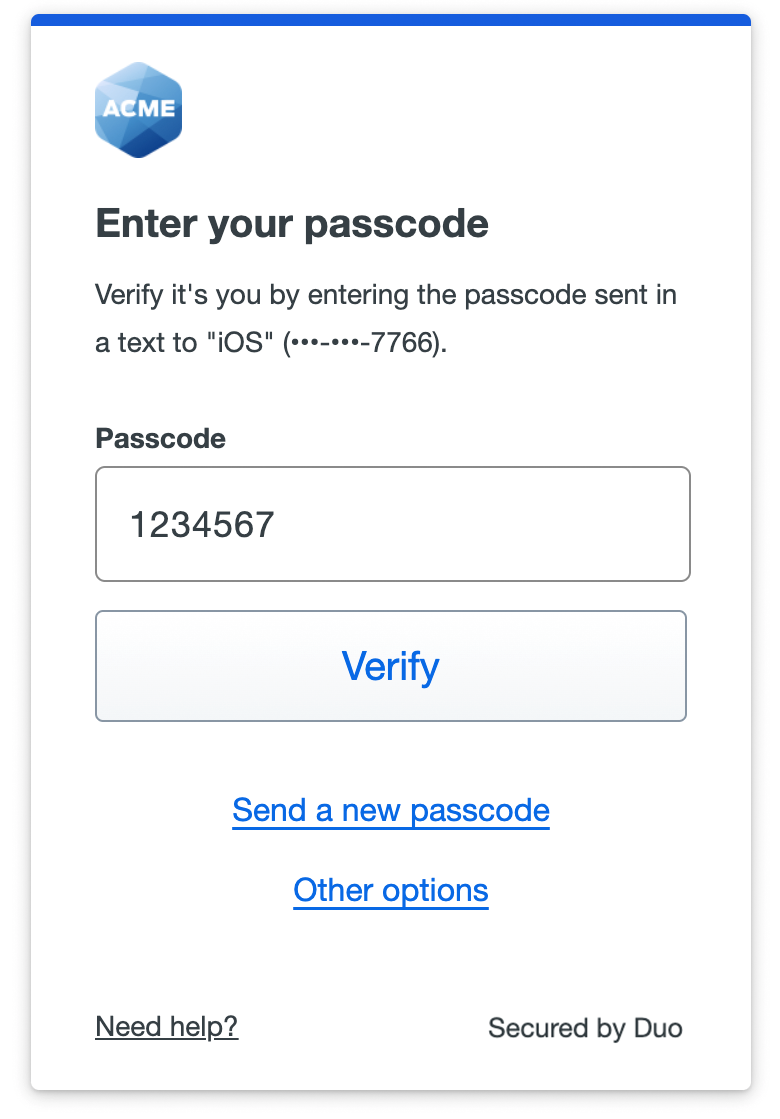
Text Message Passcode
Log in using a passcode received from Duo in a text message. When you land on the text message page, it will show that a text message was just sent to you with a passcode. When you receive the message, enter that passcode into the space provided and click or tap Verify to log in to the application.
If you did not receive the text message from Duo, use the Send a new passcode link to try sending it again.
Passcodes received in a text message expire when used.
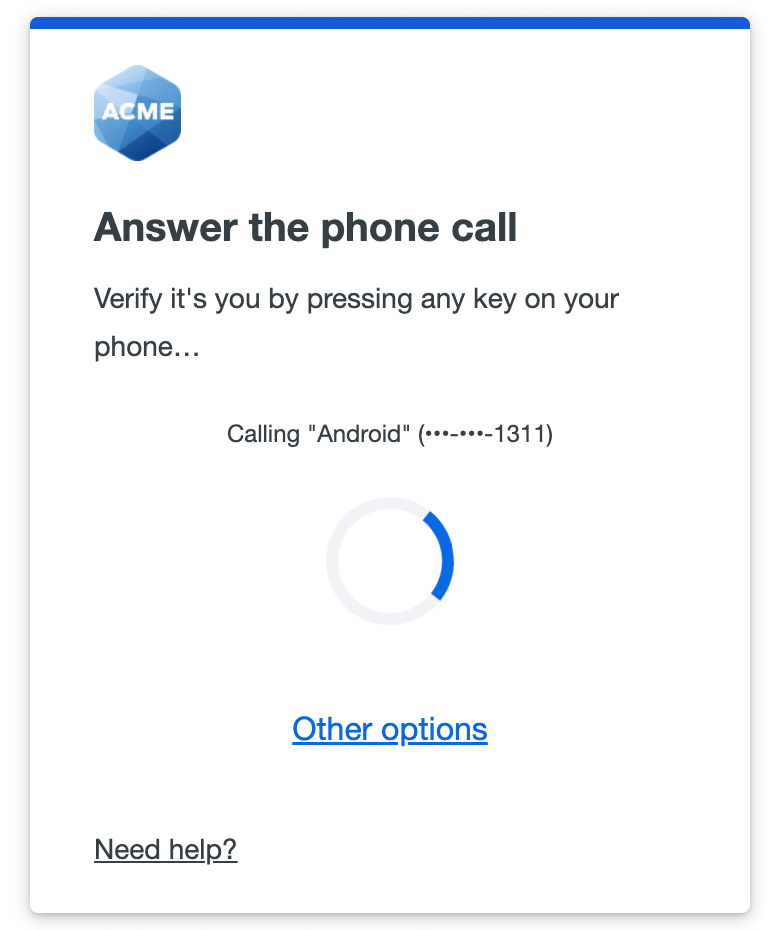
Phone Call
Authenticate via phone callback. Answer the phone call from Duo and follow the voice instructions to log in to the application.
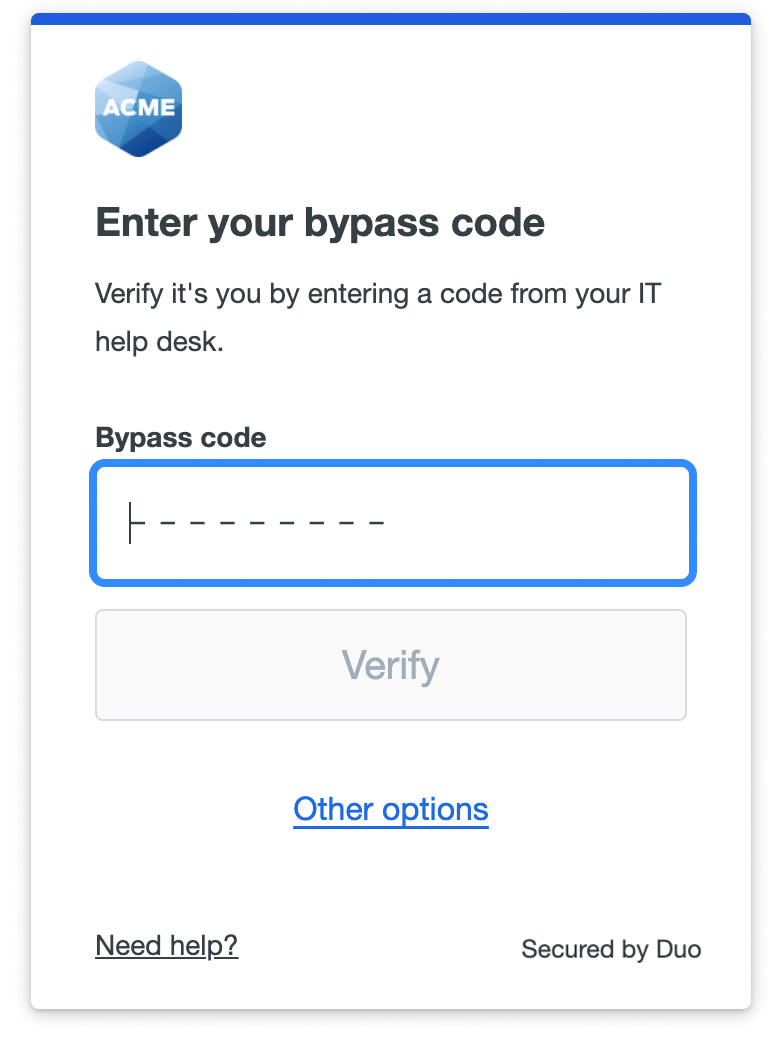
Bypass Code
Log in using a code provided by your organization’s Duo administrator or help desk. Enter that code into the space provided and click or tap Verify to log in to the application.