National Cybersecurity Awareness Month 2017: October 2-6, 2017

Highlights of Security Awareness Week
We covered several topics this week aimed at increasing security awareness and illustrating best practices. We hope you’ll use this information to be good custodians to your own information as well as any information you collect on behalf of the University. We encourage you to engage Information Security (buinfosec@bu.edu) with any questions you may have and please visit our web pages for more information!
It’s important to make sure that all of your devices (computers, tablets, phones) are properly secured. Keeping your devices up to date and secured should be your first step at protecting your data and systems from being compromised. More information on securing your devices can be found here.
- Protect Your On-Line Identity
It is critical to learn how to protect yourself and guard your privacy. As we routinely see with companies having major data breaches (Equifax being the latest in a long list), your identity and even your personal information is out there, and could be at risk. Visit our site here for tips on keeping your online identity safe.
- Don’t fall for phishing emails
Phishing is one of the most common methods used for stealing your authorization credentials or infecting your computer. There are several tips to help you spot, and avoid, phishing emails documented here
- Data Classification and Protection
The first step to making sure you are properly handing University data is to know how the data is classified. At BU, data is classified into four categories: Public, Internal, Confidential, and Restricted Use. Each category has its own set of criteria for how data can be used, stored, and shared. The University’s Data Classification Policy will help you easily identify the categories of University data in your possession.
Once you know the data’s classification, you can review the Data Protection Requirements and Minimum Security Standards to learn how you are expected to secure it.
Think of your own personal data in the same context and keep your most sensitive data private and secured.
Day 4: Know Your Data
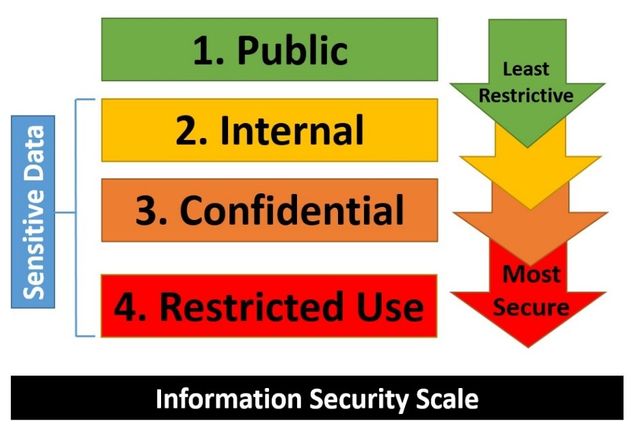
At Boston University, our data can be classified into 4 groups:
Public Data: Data that is disclosed to anyone regardless of affiliation. Examples – The published BU Directory, public websites
Internal Data: information that is potentially sensitive and is not intended to be shared with the public. Examples – procedural documentation, memos, meeting minutes
Confidential Data: Information that, if made available to unauthorized parties, may adversely affect individuals or the business of Boston University. This classification also includes data that the University is required to keep confidential, either by law (e.g., FERPA) or under a confidentiality agreement with a third party. Examples – FERPA data, BUID, salary information
Restricted Use Data: Any information that BU has a contractual, legal, or regulatory obligation to safeguard in the most stringent manner. Examples – Passwords, Social Security numbers, Driver’s License numbers, Credit Card numbers, Financial Account Information, and HIPAA data
Details on how protect our data are spelling out in our Data Protection Standards.
- You can read more about data types and classification here
- Once you know how to classify your data, you can read our guidelines on how to properly secure your data here
You should think of your own personal data the same way. It is important to know what data should and should not be made public online. Always be mindful of what you consider your most sensitive data (social security number, banking info, passwords etc) and make sure you take extra precautions to secure this information.
Information that is most critical to you (your own confidential and restricted use data) should never be shared online publically. Always keep your passwords private, and treat answers to your security questions the same. Always consider the information you’re sharing online, including family and other personal information, as it can potentially be accessed by anyone to try to gain unauthorized access to your accounts.
Day 3: How to Identify and Avoid Phishing

Cybercriminals know the best strategies for gaining access to an organization’s sensitive data. In most cases, it doesn’t involve them rappelling from a ceiling’s skylight and deftly avoiding a laser detection system to hack into your servers; instead, they simply manipulate a community member.
- Phishing isn’t just e-mail! Cybercriminals will also launch phishing attacks through phone calls, text messages, or other online messaging applications. Don’t know the sender or caller? Seem too good to be true? It’s probably a phishing attack.
- Know the signs. Does the e-mail contain a vague salutation, spelling or grammatical errors, an urgent request, and/or an offer that seems impossibly good? Click that delete button.
- Verify the sender. Check the sender’s e-mail address to make sure it’s legitimate. If it appears that a Boston University IT Support Group is asking you to click on a link to increase your mailbox quota, but the sender is “UniversityHelpDesk@yahoo.com,” it’s a phishing message.
- Don’t be duped by aesthetics. Phishing e-mails often contain convincing logos, links to actual company websites, legitimate phone numbers, and e-mail signatures of actual employees. However, if the message is urging you to take action — especially action such as sending sensitive information, clicking on a link, or downloading an attachment — exercise caution and look for other telltale signs of phishing attacks. Don’t hesitate to contact the company directly; they can verify legitimacy and may not even be aware that their name is being used for fraud.
- Never, ever share your password. Did we say never? We mean never. Your password is the key to your identity, your data, and your classmates’ and colleagues’ data. It is for your eyes only. Boston University’s IT Support Groups will never ask you for your password.
- Avoid opening links and attachments from unknown senders. Get into the habit of typing known URLs into your browser. Don’t open attachments unless you’re expecting a file from someone. Give them a call if you’re suspicious.
- When you’re not sure, call to verify. Let’s say you receive an e-mail claiming to be from someone you know — a friend, colleague, or even one of your professors. Cybercriminals often spoof addresses to convince you, then request that you perform an action such as transfer funds or provide sensitive information. If something seems off about the e-mail, call them at a known number listed in The Boston University online directory to confirm the request.
- Don’t talk to strangers! Receive a call from someone you don’t know? Are they asking you to provide information or making odd requests? Hang up the phone and report it to the IT Help Center.
- Don’t be tempted by abandoned flash drives. Cybercriminals may leave flash drives lying around for victims to pick up and insert, thereby unknowingly installing malware on their computers. You might be tempted to insert a flash drive only to find out the rightful owner, but be wary — it could be a trap.
- See someone suspicious? Say something. If you notice someone suspicious walking around or lingering behind someone else, especially in a restricted area, call Boston University Police Department at 617-353-2121.
Day 2: Managing Your Online Identity

You and your information are everywhere. When you’re online you leave a trail of “digital exhaust” in the form of browser cookies, GPS data, social network posts, and e-mail exchanges, among others. It is critical to learn how to protect yourself and guard your privacy. As we routinely see with companies having major data breaches (Equifax being the latest in a long list), your identity and even your personal information is out there, and could be at risk.
Use long and complex passwords or passphrases. These are often the first line of defense in protecting an online account. The length and complexity of your passwords can provide an extra level of protection for your personal information. You can find information on how to generate a strong password here.
Ask questions about who can access the information you are posting online, who controls and owns the information, and what is shared with third parties.
Take care what you share. Periodically check the privacy settings for your social networking apps to ensure that they are set to share only what you want, with whom you intend. Be very careful about putting personal information online.
Keep your personal information private. Assess whether it’s necessary to share personal or sensitive information such as your birthday, mailing address, phone number, e-mail, mother’s maiden name, sexual orientation, or Social Security number.
Be cautious about accepting requests to connect online. Connect only to people you know and trust to not misuse the information you post.
Read your credit card, bank, and pay statements carefully each month. Look for unusual or unexpected transactions. Remember also to review recurring bill charges and other important personal account information. Periodically review your credit reports as well!
If a request for your personal info doesn’t feel right, do not feel obligated to respond! Legitimate companies won’t ask for personal information such as your social security number, password, or account number in a pop-up ad, e-mail, text, or unsolicited phone call.
Using Wi-Fi? If only public Wi-Fi is available, restrict your activity to simple searches (no banking!) or use a VPN (virtual private network). The latter provides an encrypted tunnel between you and the sites you visit.
Should you trust that app? Only use apps from reputable sources. Check out reviews from users or other trusted sources before downloading anything that is unfamiliar.
Day 1: Welcome to Information Security Awareness Week!

Welcome to Information Security Awareness Week!
It is important these days to make sure that our devices are secure. Boston University has the Minimum Security Standards policy that defines the security requirements for devices that have University data on them. For personal devices that aren’t used for University business, here are some tips to help protect them and your personal information.
Keep your computer and applications updated. Patches or updates help resolve security flaws that you might have on your system, protecting you from malicious attempts to compromise your system. Patches should be applied on a fairly regular basis at a time that’s convenient for you.
Install antivirus software. You should install antivirus software on your personal devices. Antivirus isn’t just for laptops! It should be installed on your desktop computers, tablets, and phones! Boston University provides McAfee for free here.
Enable Encryption on your device. Your devices should be encrypted using the built in encryption feature included in your phone or computer’s operating system. For personal computers, On Mac there is FileVault and Windows there is Bitlocker.
Require a password when logging into your devices. It is always good to have a password required to login to your devices. If your device gets stolen and there isn’t a login password, then the thief would have access to all of your data immediately.
Use a secure connection (often called a “VPN”) to connect to the network. Using a secure connection provides an encrypted tunnel for information to travel from your computer and throughout the internet. This is important when you are working remotely or using public WiFi hotspots where data can potentially be read by malicious individuals if it isn’t encrypted.





